Email validation describes the checking of an email address to ensure that it is correct, active, and able to get emails. The main idea here is that if you try to send an email to somebody, the email will not vanish somewhere else but rather come to the other person's inbox. Organizations that send out newsletters, advertise, or try to engage their customers via electronic mail will add validation to their list as a first solution in the prevention of damage to their image and the maximization of their return on investment.
Then, what makes email validation a critical process? We can say that it is simply because there are invalid or fake emails that might find a way into your database. The methods used would be... typos, spam signups, or deliberate misuse of the database. Email validation is like the quality assurance of your direct line to the customers, whereby only correct and functioning email addresses come through.
Why Email Validation Matters
On the one hand, the necessity of email validation is huge. When an invalid email address is injected into your mailing list, the deliverability rate is likely to decrease with each such incident. Most of the times when you get several of your emails bounced, the services that host your email such as Gmail or Outlook will regard your domain as the source of suspicious activities and will classify your future emails as spam, or even be inaccessible from users they trust.
Another advantage of validation is it opens the door of personalization wider. The setup will look perfectly neat if the list is off and on and active your segmentation will bring better outcomes since the targets are real persons. It is very similar to cleaning your phone book where you dispose of the numbers which you are no longer in contact with and keep those who actually answer your calls.
Understanding Email Verifiers
Companies use email verifiers to help them combat the problem of invalid addresses. The hypothesis behind these tools is that an email address is needed to be real, active, and able to receive messages. They, indeed, perform the role of a security officer in all your mail promotions, filtering out those addresses that may cause you low deliverability issues.
The thing is, email verifications are not only carried out by what is in the email's name or if punctuation is okay. They become quite elaborate in a way that they dive into the domain, make sure the server is functioning and occasionally even check with the email provider if the mailbox is lively.
There are various grounds on which email verification can be categorized. For example, real-time email verification can be defined as the process during which an email is checked immediately after the entry into a form and the batch mode where the emails are verified after they have been loaded.
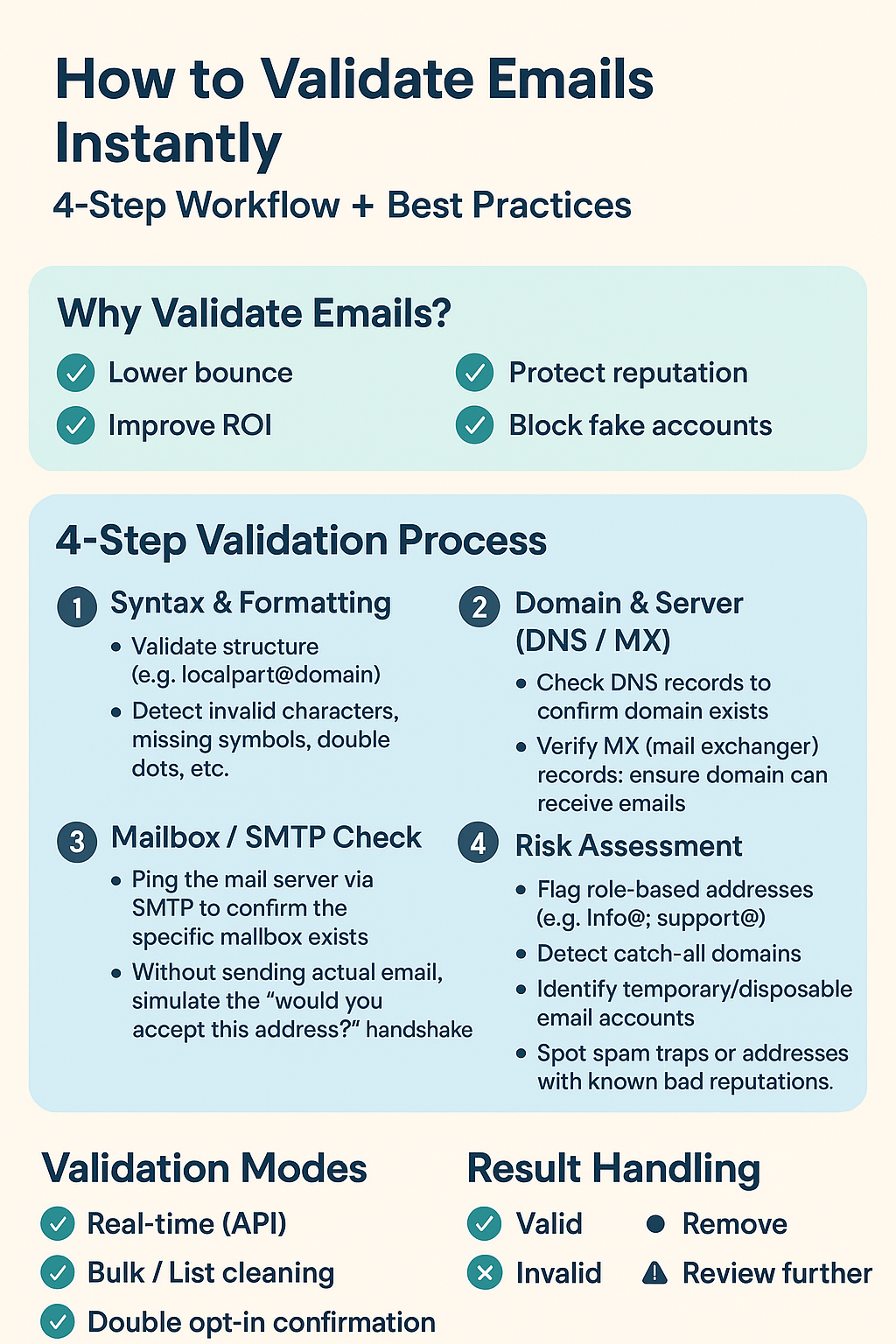
Key Features of a Reliable Email Verifier
Choosing an email verifier is more than just grabbing a random tool. A good and reliable one should not only give you the results that are detailed and accurate but also be easy to use. Just think of a car with a very powerful engine but no steering wheel – you’d be in a situation where you can’t go far and that’s how a partial email verifier works.
Those are the main features you cannot miss when examining options:
- Bulk Email Verification – If the number of emails you are dealing with is in the thousands, you must have access to a tool that can effortlessly handle large lists without the processing pace going down.
- Real-Time Verification – The function of this feature is that when an email is entered in the form, the tool immediately checks it. The comparison is like that of a club which only allows in the very people it can verify.
- Detailed Reports – The email verification tool that is really good doesn’t just give absolute answers as to whether an email is legitimate or not. It even provides the reason for the account being a catch-all domain, temporary address, or risky one.
- Integrations – Always scout for the email verifiers that are compatible with your CRM, email marketing software, or website sign-up forms. You are then liberated from the daily chore of list uploading and downloading.
Not having these features will drag you into a mood where you will be doubting your choices or simply wasting time instead of enjoying it.
Types of Email Verification Tools
Email verification tools are available in different options and the one that suits you better is the one that fits your workflow. In general, there are two main categories:
- Bulk Email Verifiers
- Are a great tool for the marketers that have large lists.
- The user uploads the email database, and the software performs the checks on all the addresses.
- Most suitable for cleaning old or purchased lists before sending out the campaigns.
- Real-Time Email Verifiers
- Directly linked with your website forms or CRMs.
- Right away check every new sign-up and only if it is valid then it is added to your list.
- Stop fake or temporary emails that are never going to be used from being a part of your system.
no2bounce provides both bulk and real-time verification allowing companies the option to have a clean list of contacts as well as to stop any new invalid entries.
Step-by-Step Guide to Validating Emails Instantly
Once you comprehend the benefits, next you will become actively engaged in these straightforward steps to instantly validate emails through a checker. These instructions will assist you with this if you are a small business goat, a marketer, or even a newsletter operator.
Step 1: Collect Your Email List
Prior to executing validation, you must ensure that your list is available. Examples of this could be:
- CRM exports
- Newsletter registrations
- Customer databases
- Purchased lists (although these are quite dangerous and usually have a lot of garbage on them)
The essential thing is to bring together all of your e-mails in one spot. Simply exporting them to a CSV or Excel file will make it easy for you to upload them into the verifier.
Step 2: Upload Your List to the Verifier
After you have the list, log into your preferred email verification tool. Most simple verifications do this step in a very user-friendly way, you just drag and drop the file into the interface.
Always keep an eye on the file formats that are allowed. The majority of the tools will work if your data is saved in CSV, TXT, or Excel files.
Step 3: Run the Verification Process
This part is when the charm takes place. The "Verify" button should be pressed after the uploading. Multiple checks will be accompanied by the tool such as:
- Syntax verification
- Domain and MX record validation
- SMTP checks
- Disposable email detection
The time for this to be completed is directly proportional to the number of your list and thus it can be from a few minutes to several hours.
Step 4: Review Verification Results
Once the verifier has finished its work, it will display the categorized results as follows:
- Valid – Safe to store
- Invalid – Delete immediately
- Catch-All – Risky; domain that is compatible with all emails, but the inbox may not exist
- Disposable – Temporary addresses; in general, these are by-products of free sign-ups
- Role-Based – The emails like info@ or sales@, which are probably not personally engaged with
This analysis will guide you in keeping only those addresses that are safe and valid.
Step 5: Clean and Update Your List
In conclusion, remove the invalid and disposable emails from your list. The distribution of usage for the catch-all and role-based mail is something you preferably decide depending on your business strategy. Some companies retain them; however, others simply delete them to be on the safer side.
After you have cleaned and updated the list, import it into your CRM or email marketing platform. From this point on, you will be handling a clean and verified database.
Common Methods of Email Verification
Email verification is not a one-step procedure, in fact, it goes through various levels of checks to prove the accuracy. The comparison to airport security is quite fitting; there you don't just go through one scanner but through various ID checks, baggage scans, and sometimes even random inspections. In like manner, email verification depends on a collection of techniques that work in unison to separate invalid addresses from the usable ones.
Syntax Check
Syntax check is the very first line of defense. This step assures that the email is in the correct format - as an example, username@domain.com. Any one of the errors like missing "@" symbol, spaces, or even characters that are not usual immediately point to the address being invalid.
It might appear to be a very minor issue, yet syntax errors occur quite frequently. Frequently, users type incorrectly when creating accounts such as "gmial.com" instead of "gmail.com." The syntax checking process is very fast to locate these mistakes, thus avoiding that erroneous addresses become part of your list.
However, one should remember that syntax check just gives a thumbs-up to the email structure but does not attest to the email's factual existence. That is the reason why it has a number of layers.
Domain/MX Record Check
Domain/MX Record Check follows the syntax check. Every email that exists has a domain attached to it and that domain should have MX records that indicate the places from where the emails can be delivered.
To illustrate, if an instance of test@abcxyz.com was set up to sign up but the domain is non-existent or does not have MX records, the email verifier can predict that it will be a hard bounce. This step is very instrumental in finding out fake and abandoned domains.
Role-Based Email Detection
Role-based emails refer to the addresses like:
- info@company.com
- support@business.org
- sales@brand.net
The main thing with them is that they are not connected with any particular individual but rather with specific departments or groups. Although they are technically valid, the number of people who access the inbox is quite high, therefore, the emails have low engagement rate. In marketing campaigns where personalization counts, role-based emails are considered as ones with potential risk.
Disposable Email Detection
One-time or disposable emails are temporary addresses created by services such as TempMail or 10MinuteMail. These are mostly used to avoid providing the actual email address while signing up for something.
Suppose you have disposable email addresses on your list; most likely, the result would be zero engagement, and after the temporary inbox expires, you would be receiving many bounces. The good ones spot these quickly and save your time and resources from being wasted.
SMTP Verification
SMTP verification is the last and most complicated stage. The process includes the "pings" procedure to the recipient's mail server, which is a check to see if a particular mailbox exists and if it can receive emails.
The procedure is similar to going and knocking on someone's door before making a delivery. If there is no answer, the conclusion is that the address is not worth keeping.
This step is indispensable since, in some cases, certain domains are set in such a way that all messages (catch-all) can be accepted, thus making it hard to find out whether the inbox is real or not. However, SMTP verification adds another point of confirmation to the system.
Choosing the Right Email Verifier
There are numerous email verification tools out there and choosing one can turn out to be quite a daunting task. The secret lies in seeing past the stylish adverts and only focusing on what really counts—accuracy, speed, integrations, and being cost-effective.
What to look for before deciding:
While buying an email verification tool, keep these essential factors in mind:
- Accuracy Rate – Is the tool able to produce the same accurate results each time? Even a small proportion of errors can have a significant impact on your campaign.
- Speed – Can it process large lists in a short time without getting a crash or slowdown?
- Ease of Use – A user-friendly interface facilitates the learning process for new users.
- Integrations – Can it link up with your CRM, email marketing tools, or sign-up forms?
- Security & Compliance – Find out if the tool complies with GDPR and if the data is encrypted while being handled.
- Pricing Plans – Some of them will ask for a payment per email verified, whereas the others will offer you monthly subscriptions. Select the one that suits your volume requirements the most.
How Businesses Benefit from Real-Time Email Verification
Real-time email verification brings different benefits in each industry. Let's explore the ways this tool can help a company to grow by sector.
SaaS Companies
Software-as-a-Service (SaaS) companies are mostly powered by the use of free trials and sign-ups. However, the use of fake or temporary emails not only wastes the server resources but also leads the company to a dead-end road in creating quality leads.
Once they start the process of email verification at the sign-up stage, SaaS companies will have a cleaner filtered list of genuine prospects and hence will be able to enhance lead nurturing and decrease churn rate.
Marketing Agencies
Agency clients regularly provide long lists for their campaigns that agencies manage. The occurrence of high bounce rates inflicts deliverability that is just one aspect of the problem. More importantly, it can also harm the agency's reputation with clients.
Agencies who have incorporated the use of verification tools into their strategies can access and use cleaner data for a longer period, obtain better campaign results, and earn client loyalty.
Financial Services
Banks, insurance firms, and investment platforms are the types of businesses that rely heavily on emails to communicate securely with their customers. The presence of invalid or fake emails in their system not only causes bouncing issues but also brings security loopholes.
Email verification is the key that opens the door to confidential and secure information flow between financial institutions and their rightful clients thus ensuring adherence to standard regulations and building up trust among customers.
Conclusion
Real-time email validation through an email verification tool is not just a simple technical task, it is a step that leads to a number of other advantages like enhancing your deliverability rate, keeping your sender reputation safe and making better use of your marketing budget. The most efficient way to accomplish this task is by implementing a well-planned process of validation.
This way, companies will get their emails to the right people who are truly interested in their content and thus they will experience a reduction in their bounce rates and also be free from the danger of spam. Although the process of incorporating email verification as part of your routine may seem like a small-scale activity, it actually reaps major benefits for you in the long run as you are able to keep your email list both clean and reliable, and maintain authentic relationships with your customers.
Start cleaning your list instantly.
No credit card required.

.jpg)
